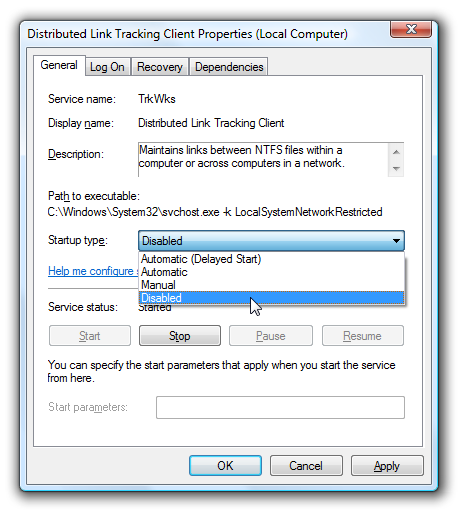
Administrator Password Guessing
Performing Automated Password Guessing
Legion
NTInfoScan
Defending Against Password Guessing
Monitoring Event Viewer Logs
VisualLast
Eavesdroppin on Network Password Exchange
Hacking Tool: L0phtCrack
Hacking Tool: KerbCrack
Privilege Escalation
Hacking Tool: GetAdmin
Hacking Tool: hk
Manual Password Cracking Algorithm
Automatic Password Cracking Algorithm
Password Types
Types of Password Attacks
Dictionary Attack
Brute Force Attack
Distributed Brute Force Attack
Password Change Interval
Hybrid Attack
Cracking Windows 2000 Passwords
Retrieving the SAM file
Redirecting SMB Logon to the Attacker
SMB Redirection
Hacking Tool: SMBRelay
Hacking Tool: SMBRelay2
SMBRelay Man-in-the-Middle (MITM)
SMBRelay MITM Countermeasures
Hacking Tool: SMBGrinder
Hacking Tool: SMBDie
Hacking Tool: NBTDeputy
NetBIOS DoS Attack
Hacking Tool: nbname
Hacking Tool: John the Ripper
LanManager Hash
Password Cracking Countermeasures
Keystroke Logger
Hacking Tool: Spector
AntiSpector
Hacking Tool: eBlaster
Hacking Tool: SpyAnywhere
Hacking Tool: IKS Software Logger
Hardware Tool: Hardware Key Logger
Hacking Tool: Rootkit
Planting Rootkit on Windows 2000 Machine
_rootkit_ embedded TCP/IP Stack
Rootkit Countermeasures
MD5 Checksum utility
Tripwire
Covering Tracks
Disabling Auditing
Auditpol
Clearing the Event Log
Hacking Tool: Elslave
Hacking Tool: Winzapper
Hacking Tool: Evidence Eliminator
Hidding Files
NTFS File Streaming
Hacking Tool: makestrm
NTFS Streams Countermeasures
LNS
Steganography
Hacking Tool: ImageHide
Hacking Tool: MP3Stego
Hacking Tool: Snow
http://rapidshare.com/files
http://rapidshare.com/files
http://rapidshare.com/files
Wednesday, June 4, 2008
System hacking
Posted by windows team at 6:02 AM 368 comments
Automatically Search and Download Lyrics of Favourite Songs Inside Winamp or Mediaplayer
Are you tired of searching lyrics of your favorite songs.Normally we do it by first googling the title of the song and then visiting the lyrics page...copy..paste..save..:(
But with this small Lyrics Plugin it's so simple...Just add this plugin to your Winamp or Windows Media Player and all the rest it does by itself..Just start listening to your favourite songs and lyrics will be displayed automatically.Also you can add lyrics by yourself if the plugin is unable to find them.
Direct Links:
Posted by windows team at 6:01 AM 4 comments
Latest Airtel Free GPRS Unlimited Using Browser Hack May 2008

So another hack been found out for free Unlimited Gprs for Airtel live users.The new trick for Airtel free internet is by using a browser called teashark or Ucweb.Follow the steps below for unlimited mobile browsing.
Download Teashark browser(for MIDP 2.0 handsets only) from here or from here if you are using mobile browser( Wap link also given below )
Install the browser and select Airtel Live as the access point and start browsing absolutely free.(Don't worry airtel won't charge you ......:)
If Teashark browser doesn't work then go for Ucweb browser which can be downloaded from here.They also have many features like inbuild download manager,search function,email service and also page saving options.
Download Teashark Browser (Download to PC) Wap link
Download UCWeb Browser (Download to PC) Wap link
I am presently checking whether it is possible to connect and browse in PC using this new Airtel Hack. If you have any problems configuring free gprs then just comment here.
Posted by windows team at 6:00 AM 3 comments
Bluetooth Applications for Your Mobiles
Bluetooth Applications to make ur Mobile Rocking..
This pack contains some of the best bluetooth applications like :-
FTP Superbluetooth hack 1.07,1.08;
Freejack,
Networker,
MobiLuck,
BT Explorer,
BT Enhancer etc..
Bluetooth Enhancer :More than one blue tooth connection at one time....
MobiLuck : also Named "Bluetooth Hunter"…Returns alert on the presence of Bluetooth near to you.
BlueJackX : spy work,and is work resorted,and steals files of the other device through Bluetooth.
Networker : Make it work in Conjugation with Mobiluck and see the magic :D
Nokia Data Transfer : Awesome application to transfer the entire DATA to another device By Bluetooth.
DreamChat : Chat through Bluetooth with Dream Chat.
FTP Super Bluetooth Hack : Program to control and read informations from other phone>>> http://www.4shared.com/file
Posted by windows team at 5:59 AM 0 comments
BEST WINDOWS TRICKS
After installing Nokia or Sony Ericsson PC Suite you might have noticed an icon being generated in your My Computer window.I frequently connect my Sony Ericsson P1i to my computer but for transferring files I use the File transfer mode in the phone which allows me use my memory card as an external drive.I have never used this icon to interact with it which lead to the question how I could remove that Sony Ericsson file manager icon in My Computer.

Also I wouldn't like to uninstall the PC Suite from my system since I might use them for firmware updation and so on.The Nokia Phone Browser entry in My Computer is connected to the PhoneBrowser.dll and all that has to be done is to unregister the dll in windows to remove the entry in My Computer.
In the Command prompt(press window key + R and type cmd) go to the folder where you installed the PC suite.This is done by typing cd "location of the folder" in the command prompt.In my case it is
Nokia Phones
cd E:\Program Files\Nokia\Nokia PC Suite 6
Now to unregister the dll and to remove the icon from my computer just use this command “regsvr32 /u PhoneBrowser.dll”. Now refresh the My Computer window and notice the changes.
Sony Ericsson Phones
Dll to be unregistered in this case is FM.dll
E:\Program Files\Sony Ericsson\Mobile4\File Manager>regsvr32 /u FM.dll

Update for Nokia phones:
To undo this(to register the dll again) just type
regsvr32 PhoneBrowser.dll
Update for Sony Ericsson Phones:
To undo this(to register the dll again) just type
regsvr32 FM.dl
Posted by windows team at 5:57 AM 0 comments
RESTRICTIONS IN WIN XP
If you want to make restrictions to what users can do or use on their computer without
having to run Poledit, you can edit the Registry. You can add and delete Windows
features in this Key shown below.
Zero is Off and the value 1 is On. Example: to Save Windows settings add or modify
the value name NoSaveSettings to 0, if set to1 Windows will not save settings. And
NoDeletePrinter set to 1 will prevent the user from deleting a printer.
The same key shows up at:
HKEY_USERS\(yourprofilename)
cies\Explorer so change it there also if you are using different profiles.
1.Open RegEdit
2.Go to HKEY_CURRENT_USER\Software
3.Go to the Explorer Key (Additional keys that can be created under Policies are
System, Explorer, Network and WinOldApp )
4.You can then add DWORD or binary values set to 1 in the appropriate keys for ON
and 0 for off.
NoDeletePrinter - Disables Deletion of Printers
NoAddPrinter - Disables Addition of Printers
NoRun - Disables Run Command
NoSetFolders - Removes Folders from Settings on Start Menu
NoSetTaskbar - Removes Taskbar from Settings on Start Menu
NoFind - Removes the Find Command
NoDrives - Hides Drives in My Computers
NoNetHood - Hides the Network Neighborhood
NoDesktop - Hides all icons on the Desktop
NoClose - Disables Shutdown
NoSaveSettings - Don't save settings on exit
DisableRegistryTools - Disable Registry Editing Tools
NoRecentDocsMenu - Hides the Documents shortcut at the Start button
NoRecentDocsHistory- Clears history of Documents
NoFileMenu _ Hides the Files Menu in Explorer
NoActiveDesktop - No Active Desktop
NoActiveDesktopChanges- No changes allowed
NoInternetIcon - No Internet Explorer Icon on the Desktop
NoFavoritesMenu - Hides the Favorites menu
NoChangeStartMenu _ Disables changes to the Start Menu
NoFolderOptions _ Hides the Folder Options in the Explorer
ClearRecentDocsOnExit - Empty the recent Docs folder on reboot
NoLogoff - Hides the Log Off .... in the Start Menu
NoViewOnDrive – Restrict a drive to open
And here are a few more you can play with
ShowInfoTip
NoTrayContextMenu
NoStartMenuSubFolders
NoWindowsUpdate
NoViewContextMenu
EnforceShellExtensionSecurity
LinkResolveIgnoreLinkInfo
NoDriveTypeAutoRun
NoStartBanner
NoSetActiveDesktop
EditLevel
NoNetConnectDisconnect
RestrictRun - Disables all exe programs except those listed in the RestrictRun subkey
This key has many other available keys, there is one to even hide the taskbar, one to
hide the control panel and more. I'm not telling you how, as someone may want to
play a trick on you. The policies key has a great deal of control over how and what
program can run and how one can access what feature.
In the System key you can enter:
NoDispCPL - Disable Display Control Panel
NoDispBackgroundPage - Hide Background Page
NoDispScrSavPage - Hide Screen Saver Page
NoDispAppearancePage - Hide Appearance Page
NoDispSettingsPage - Hide Settings Page
NoSecCPL - Disable Password Control Panel
NoPwdPage - Hide Password Change Page
NoAdminPage - Hide Remote Administration Page
NoProfilePage - Hide User Profiles Page
NoDevMgrPage - Hide Device Manager Page
NoConfigPage - Hide Hardware Profiles Page
NoFileSysPage - Hide File System Button
NoVirtMemPage - Hide Virtual Memory Button
In the Network key you can enter:
NoNetSetup - Disable the Network Control Panel
NoNetSetupIDPage - Hide Identification Page
NoNetSetupSecurityPage - Hide Access Control Page
NoFileSharingControl - Disable File Sharing Controls
NoPrintSharing - Disable Print Sharing Controls
In the WinOldApp key you can enter:
Disabled - Disable MS-DOS Prompt
NoRealMode - Disables Single-Mode MS-DOS
Hidden Programs In Windows Xp
1- Private Character Editor
This program is for designing icons and Characters(Alphapet)
Click :start
Then :run
type :EUDCEDIT
..............................
2- iExpress
This Program is for conerting your files to EXCUTABLE files
Click : start
Then : run
type : iexpress
..............................
3-Disk Cleanup
This program used for cleaning harddisk to offer space
Click : start
Then : run
type : cleanmgr
..............................
4-Dr Watson
This program Is for repairing problems in Windows
Click : start
Then : run
type : drwtsn32
..............................
5-Windows Media Player 5.1
Opens the old media player
Click : start
Then : run
type : mplay32
..............................
Program ............. CODE
__________ __________
Character Map = charmap
DirectX diagnosis = dxdiag
Object Packager = packager
System Monitor = perfmon
Program Manager = progman
Remote Access phone book = rasphone
Registry Editor = regedt32
File siganture verification tool = sigverif
Volume Contro = sndvol32
System Configuration Editor = sysedit
Syskey = syskey
Microsoft Telnet Client = telnet
XP Secrets...
Defrag
Secret - Hidden Command Line Switch
Instructions - Go to "Start", "Run" and Type defrag c: -b to defragment the Boot and Application Prefetch information.
Notes - Windows XP will run this automatically every three days or so, during system idle periods. BootVis will evoke this when you run the "Optimize System" function. There is no need to manually run this unless you wish to immediately optimize a newly installed application's load time.
For Paint
Secret - Image Trails
Instructions - Open an image and hold down Shift then drag the image around to create an image trail.
Secret - 10x Zoom
Instructions - Open an image and select the magnifying glass icon. Left-Click exactly on the line below the 8x.
The above 2 tricks works.. and i have checked...
Free Cell Cheat Code:
Secret - Instant Win
Instructions - Hold down Ctrl + Shift + F10 during game play. Then you will be asked if you want to Abort, Retry or Ignore. Choose Abort, then move any card to instantly win.
Secret - Hidden Game Modes
Instructions - In the "Game" menu choose "Select Game". Enter -1 or -2 to activate the hidden game modes.
Solitaire Cheat Code:
Secret - Instant Win
Instructions - Press Alt + Shift + 2 during game play to instantly win.
Secret - Draw single cards in a Draw Three game
Instructions - Hold down CTRL + ALT + SHIFT while drawing a new card. Instead of drawing three cards you will only draw one. delete
Posted by windows team at 5:54 AM 0 comments
How To Find WINDOWS XP CD-KEY in 10 seconds
How To Find WINDOWS XP CD-KEY in 10 seconds
insert your xp cd
browse to the i386 folder
find and open unattended.txt
scroll down to see the cd-key
Posted by windows team at 5:52 AM 0 comments
How an anti-virus program works
Do have an anti-virus program.
How can you test that it works?
This is a good question and it is wise to familiarize yourself with how your anti-virus software behaves when it detects a virus, before it really happens. One quick way to do this is to use the EICAR Anti-Virus Test File. This is a test file that will cause no damage to your system and still allow you to test if anti-virus tool is awake.Here are some steps:
1. Open a text editor (e.g. Notepad)
2. Enter the following text in it:
X5O!P%@AP[4\PZX54(P^)7CC)7}$EICAR-STANDARD-ANTIVIRUS-TEST-FILE!$H+H*
3. Save the file as EICAR.COM on your desktop.
4. Open DOS and try to execute this .COM file (or simply double-click the file on Desktop)If your anti-virus software is working properly, it will warn you that a virus has been detected when you attempt to run the .COM file.
To be double-sure, zip this file, and then try double-clicking on the ZIP file to see if your AV tool recognized viruses inside ZIP files.
You can also send this file to yourself as an attachment, just to verify if your AV tool has command of email cleanliness.
This works...
Posted by windows team at 5:51 AM 0 comments
What is svchost.exe And Why Is It Running?
According to Microsoft: "svchost.exe is a generic host process name for services that run from dynamic-link libraries". Could we have that in english please?
Some time ago, Microsoft started moving all of the functionality from internal Windows services into .dll files instead of .exe files. From a programming perspective this makes more sense for reusability… but the problem is that you can't launch a .dll file directly from Windows, it has to be loaded up from a running executable (.exe). Thus the svchost.exe process was born.
Why Are There So Many svchost.exes Running?
If you've ever taken a look at the Services section in control panel you might notice that there are a Lot of services required by Windows. If every single service ran under a single svchost.exe instance, a failure in one might bring down all of Windows… so they are separated out.
Those services are organized into logical groups, and then a single svchost.exe instance is created for each group. For instance, one svchost.exe instance runs the 3 services related to the firewall. Another svchost.exe instance might run all the services related to the user interface, and so on.
You can trim down unneeded services by disabling or stopping the services that don't absolutely need to be running. Additionally, if you are noticing very heavy CPU usage on a single svchost.exe instance you can restart the services running under that instance.
The biggest problem is identifying what services are being run on a particular svchost.exe instance… we'll cover that below.
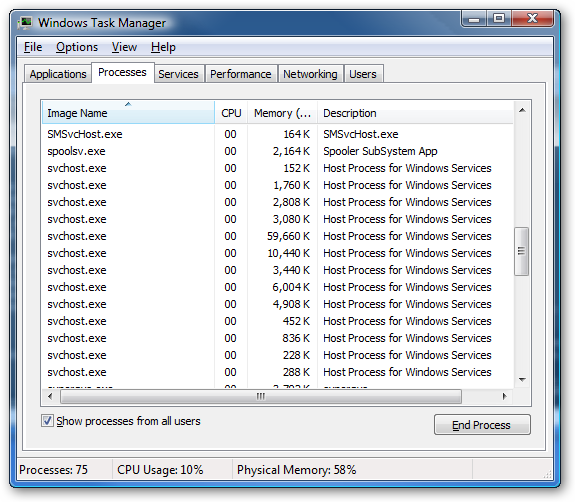
If you are curious what we're talking about, just open up Task Manager and check the "Show processes from all users" box:
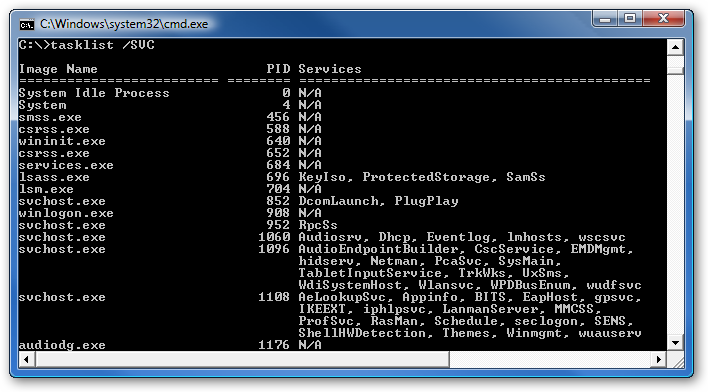
If you want to see what services are being hosted by a particular svchost.exe instance, you can use the tasklist command from the command prompt in order to see the list of services.
type: tasklist /SVC
Checking in Task Manager in Vista
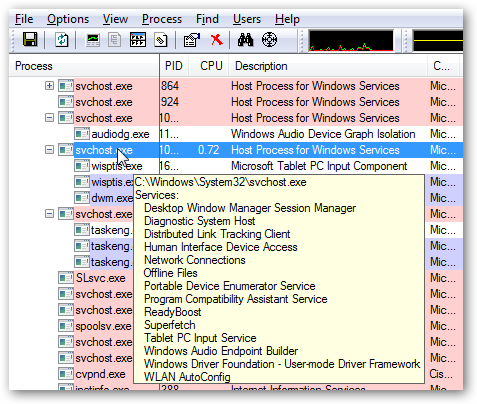
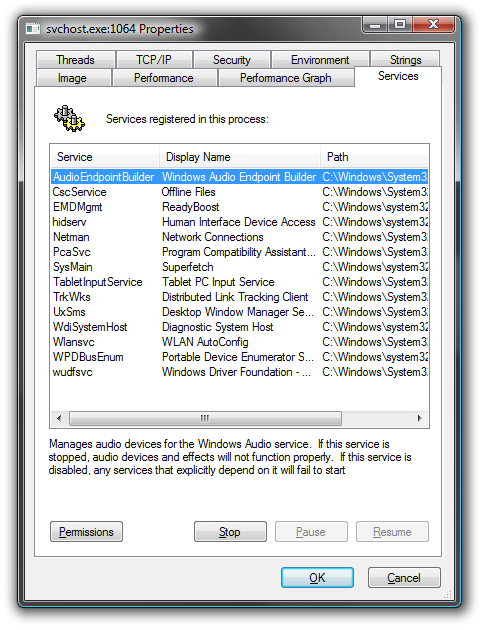
Using Process Explorer in Vista or XP
Hopefully this helps somebody!
Posted by windows team at 5:50 AM 0 comments
Boot Your PC in Style
Note : I recommend making a copy of you "Boot.ini" first, just in case you do something wrong and your window is not booting, restart and when your pc is in post(the black screen) press F8 and boot in safe mode, and replace the "Boot.ini" with your backup of "Boot.ini" and it should get back to its former state.
All of us are accustomed to seeing the Windows XP logo at system startupbut how about getting a custom message at first before the logo appears?
Heres how to do it. Its easy and simple.
Please don't mess it up until n unless you're DUMB enough.
Click start,then run.
Type c:\boot.ini
Erase whatever is there and copy and paste this
[boot loader]
timeout=5
default=multi(0)disk(0)rdisk(0)partition(1)\WINDOWS
[operating systems]
multi(0)disk(0)rdisk(0)partition(1)\WINDOWS="Write your message"/fastdetect
C:\="write your message"
Write whatever you want in between the quotes this will display for 5 seconds before windows starts
*if you have installed windows in any partition other than C:
replace the number after the last brackets of multi(0)disk(0)rdisk(0)partition(1)
Use1 for c:\
2 for d:\ and
so onIf you want to create more lines just writed:\="......"e:\="....."
After editing the file "Boot.ini" save it and restart the system to see how it goes.
Sample:
[boot loader]
timeout=10
default=multi(0)disk(0)rdisk(0)partition(1)\WINDOW S
[operating systems]multi(0)disk(0)rdisk(0)partition(1)\WINDOWS="This PC will blow in"/fastdetect
C:\="10 seconds"
D:\="Shut it down"
E:\="Or run for your LIFE"
Try it and next time when friends comes to see your PC I bet they will be astonished
Posted by windows team at 5:48 AM 0 comments
Recover deleted files from corrupt USB thumb drives,Memory cards and Hard disks
Have your USB drives become corrupt or deleted your files or formatted your USB Pen drives accidentally without knowing and thought that all the files in the drive are gone forever.But in the actual case the file is still alive and it’s recoverable only if the disk hasn’t been overwritten.Only the pointer to that file is being actually deleted and the windows thinks that there is an empty space and writes over them.When a file is deleted, it is removed from the file system. However, the actual data is not erased.Sometimes after unsafe eject of your USB drives it might show that "Drive not formatted.Format it now".Doing so will destroy all your data that moment itself and you are forced to recover that deleted files.
According to Lexar tech support, there is a bug with Windows 2000 (that MS never bothered to fix) and can corrupt the drive when it is removed without proper eject. They recommend EasyRecovery Pro for data recovery which did allow me to recover some files (> 500) using their RAW data recovery program (all other tool failed because usually said "no recognizable file on disc").
See how Linux could save your data from a corrupt USB hard drive at LinuxJournal:How a Corrupted USB Drive Was Saved by GNU/Linux
CD/DVD Data recovery
CD/DVD Data Recovery is an easy-to-use tool to recover corrupted file from CD and DVD, It fast scans disk sectors, rescues the damaged files and copies the correct data to hard disk as possible as it can. The program is especially effective for corrupted digital multimedia files, audio, video, image files, MPEG, AVI, RM, MP3, JPEG etc, and for damaged document and text files. It supports many types of optical disk such as CD-ROM, CD-R, CD-RW, DVD-ROM, DVD-R, DVD-RW and file systems such as ISO9660 and UDF.
Download click here
Undelete Plus (recover files from memory cards and usb drives)
Undelete Plus is a quick and effective way to retrieve accidentally deleted files, files removed from the Recycle Bin, in a DOS window, from a network drive, from Windows Explorer with the SHIFT key held down.The program supports all Windows file systems for hard and floppy drives including FAT12/16/32,NTFS/NTFS5 and image recovery from CompactFlash, SmartMedia, MultiMedia and Secure Digital cards.
Recuva Freeware
Recuva.exe is only 180KB and it doesn’t require any other DLL files. You can copy recuva.exe to your thumb drive and run it from there.
The inteface is very simple without any settings needed. Just select the drive that you want to scan and click on the Scan button.(referer raymond blog)
Posted by windows team at 5:47 AM 8 comments
13 of the Best Ways to Speed up your PC
Say that you wake up and want to check the traffic before you head out the door. You turn on your computer and wait. And wait. Finally you give up and decide to make some coffee, toast a bagel, and maybe grab the newspaper and check out the crossword puzzle. By the time you finally return, your computer has just completed its leisurely start up. Sound a little too familiar? While a complete computer overhaul might not be too far off, there are a few things that you can do in the meantime if a new computer isn’t in your budget. Here are a few tips for giving your computer a speed boost.
Defragment: If your computer is running slowly it may be because your files are scattered all over your hard drive. When you save a file on your computer it goes to the first available space on your hard drive. When that gets filled up it stores other parts of your file in the next available place, then the next place, and so on. When files become fragmented like this, the computer has to spend time searching the hard drive to piece them back together. This process slows you and your system down. Luckily, this is a fairly easy fix. Simply follow these steps: For a PC, go to Start menu and open your Programs menu. From there go to Accessories then Program Tools. You should see the icon for the Disk Defragmentation program in that menu. Simply click on it and windows will begin the defrag process. Be advised, however, that this process usually takes a long time so it could be something you set up to run before you go to bed or before you go to work in the morning.
Clean Up Registry: Not everyone agrees that a PC registry clean-up is much of a help, but it can’t hurt to try if you’re frustrated with your computer speed. Before you do anything to your registry, however, make sure you have it backed up as making changes to the registry can have big affects on how your computer runs. Don’t delete things from the registry when you are unsure of the function, as it can wreck havoc on your computer. Be cautious and try to use a free registry-cleaning program like CCleaner, which will not only clean out your registry but it will take care of several of some other issues listed here as well.
Remove Old Programs: Have things installed on your computer that you haven’t used in ages? Do you even know what’s installed on your computer? It’s possible all these old programs could clog up your hard drive and slow your computer down. Go to your Start menu and select the Control Panel and then Add or Remove programs. It will bring up a list of all the programs that are installed on your computer and also tell you how often you use them. If the answer is “never,” you can most likely safely uninstall the programs and free up valuable space.
Keep Spyware in Check: Spyware seems to be almost unavoidable these days for anyone who uses the Internet. Virus protection programs often catch the worst culprits but there is always something that sneaks through, and these culprits can slow your computer down. If you think you might have a spyware infection, or if you just want to be on the safe side, you can use a free program like AdAware to check your computer for spyware.
Repair Disk Errors: While defragmentation might take care of the worst of your disk problems, you can also be slowed down by errors in other places on your disk drive. As you store and delete files on your hard drive, bad sectors can develop. These sectors can make accessing or saving files difficult and they can slow your computer down. You can check for problems by running another Windows utility. Go to your Start menu and click on My Computer. When the My Computer window comes up right click on the drive you want to check for errors. When the drop down menu shows up go to properties. This will bring a box up and you’ll click on Tools. Check the box that says scan and attempt recovery of bad sectors then click start. Once this is done you’ll be given the option to fix the bad sectors, and you’ll want to select “yes.” Fixing any bad areas in your drives can add some significant speed to your system.
Get Rid of Temporary Files: Windows is notorious for storing temporary files that can clog up your hard drive and slow down your computer. These temporary files aren’t going to go anywhere unless you ask them to, and that’s where the disk cleanup tool can come in handy. To run an automatic disk cleanup just go to Programs under your Start menu. It’s under Accessories and then System Tools. There you should see the icon for disk cleanup. You’ll simply need to run the cleanup program and it will determine what you can safely get rid of on your computer (this will usually be just temporary files and things you’ve yet to empty from the recycle bin). You’d be surprised how much room you can free up by eliminating these files.
Clean Up Your Desktop: Some of you, and you know who you are, have virtual desktops that are just as messy as your real desktops. This may not seem like a big deal, but it’s important enough that windows will give you little nudging reminders to clean up your desktop (which, if you’re like me, you promptly ignore). Go through all the stuff you have on your desktop, delete the shortcuts you no longer use, and organize all the remaining miscellaneous files.
Clear your Inbox:If you’re using Outlook or Outlook Express as your email client you might want to check to see just how many old emails you have hanging around. These could be clogging up your memory and causing your computer to run more slowly than it should. If you haven’t checked that spam folder it could chock full of computer-clogging waste. Go through your old emails and weed out those emails that you might not actually need.
Reinstall Windows: If you’re getting desperate for a computer fix, and if you have the time to spend, a Windows reinstall can be one option to speed up your system. Make absolutely sure you’ve backed up any data that’s important to you before you begin, otherwise those files be lost. Then you can begin to wipe the slate clean, reformat your hard drive, reinstall your applications, and put your files back onto your computer from the backup. You’ll be eliminating years of junk that can slow down your system. The basic reinstallation is fairly simple if you use the recovery disk that came with your computer; but reinstalling all your applications can take a long time, so be prepared.
Check for Viruses: You can never be quite sure what is lurking on your computer, so make sure your anti-virus program has the latest updates, and run a full scan of your computer. Virus programs can often disguise themselves as legitimate windows applications so they can be hiding out in places you might not have noticed. If you don’t have an anti-virus program (shame on you!) you can try a free one like Avast!.
Stop Unnecessary Services: Often when you install a new program it will add itself to the programs that start automatically when your computer boots up. All of these unnecessary programs can slow down your startup. You can disable these programs by going to the start menu and then click on Run. Type “msconfig” in the box that comes up. Click on the Startup tab and you’ll be able to see all the pesky programs that bog down your startup time. Get rid of anything that doesn’t look absolutely necessary, but be careful to avoid any Windows system components.
Install Updates: Keeping your computers operating system and drivers up to date is very important in maintaining performance. Updates also help make your computer more secure and reliable, improving performance indirectly as well. Most Windows updates can be downloaded from the Internet and installed (mine does this automatically) but you can use the Windows Update site to gain access to the updates as well. This site is accessible only if you’re running Internet Explorer (IE).
Delete Old Network Connections: Another thing to check that might slow your computer down is old network connections. Your computer will waste time searching for old drives and ports that no longer exist. You can delete these connections by going into your control panel and selecting Network Connections. You should find a list of all the networks your computer recognizes, and you can delete those that are no longer necessary.
Technology is supposed to make your life easier, not more irritating. Hopefully, some of these tips will help you shave at least a few minutes off the time it takes for your computer to get going, whether just starting up or when you try to run a program (or multiple programs). But, if you’d tried all of these tips and your computer still refuses to kick it up a notch, it might be time to send it to the computer heaven. But don’t give up without a fight without trying all of these tips.
Unlike a new computer purchase, these tips are free, so you’ve got nothing to lose.But, if it’s time for a new computer, be smart about how you purchase one. Look for deals where you can pay over time with no interest, or use a card that has 0% APR. Then sock that monthly payment away in a savings account until it comes due. You’ll save a little money on this high-ticket item, and you’ll have a tax write-off if you use it for business. Keep this list of tips around, and you may never have a slow-down problem with your new computer
Posted by windows team at 5:43 AM 0 comments
How to Write a Windows XP Driver
How to Write a Windows XP Driver
Summary: This document describes the steps you should take to create a Microsoft® Windows® XP driver for your device.
To create a Windows XP device driver:
1. Install the current Windows DDK. Read the system requirements and installation instructions in the stand-alone Getting Started HTML file supplied with the DDK.
2. Read Getting Started with Windows Drivers. This document guides you through the planning and decision-making process involved in making a Windows device driver from design through distribution. You should also look through the DDK documentation for device-type-specific information.
The DDK documentation set has the following device-type-specific nodes:
· Battery Devices
· Display and Print Devices
· IEEE 1284.4 Devices
· Interactive Input Devices
· Modem Devices
· Multifunction Devices
· Network Devices and Protocols
· Parallel Ports and Devices
· Serial Ports and Devices
· Smart Card Devices
· Still Image Devices
· Storage Devices
· Streaming Devices (Video and Audio)
· Devices Requiring VDDs
3. IDE bus are described in System Support for Buses. Driver development for most device types also requires a strong understanding of Windows operating system fundamentals, which are described in Kernel-Mode Driver Architecture.
4. Look through the driver source code provided with the DDK for a sample that represents your device type. Use the sample code where possible, modifying it for your device's specifics.
5. The sample code can enhance your understanding of Windows XP driver implementation requirements and speed your development time.
6. Compile and build your driver. This should be done using the Build utility and not some other compiler, because the Build utility has certain features that are necessary for driver development.
7. Obtain a checked build of Windows XP, so that you can test and debug your driver using free and checked system builds.
8. The checked build of Windows XP provides extensive kernel-mode debugging capabilities not available in the free build.
9. Create an INF file so that you can install and test your driver.
10. Test and debug your driver. You should use Driver Verifier, a program that puts your driver through a variety of tests, stresses, and deliberate failures in order to test its response and reliability in many extreme situations. You should also use a debugger. Microsoft provides several powerful debuggers that can monitor and debug kernel-mode and user-mode drivers. Using Driver Verifier in conjunction with these debuggers, on both the checked and free versions of the operating system, can be a powerful way to test your driver.
11. Provide an installation package so that customers can install devices that use your driver.
12. Submit your driver and installation package to Microsoft so that it can be digitally signed.
There are many resources available to you while developing your driver. The following sites describe some of the support available to you:
a. http://www.microsoft.com/ddk describes how to obtain the current DDK and provides other information, such as a driver development reading list.
b. http://www.microsoft.com/hwdev provides information, such as device-type-specific white papers and late-breaking news, and a list of resources available to driver developers.
c. http://support.microsoft.com/support/ddk contains DDK product support information.
Posted by windows team at 5:37 AM 0 comments
Boot Winxp Fast
Boot Winxp Fast
Follow the following steps
1. Open notepad.exe, type "del c:\windows\prefetch\ntosboot-*.* /q" (without the quotes) & save as "ntosboot.bat" in c:\
2. From the Start menu, select "Run..." & type "gpedit.msc".
3. Double click "Windows Settings" under "Computer Configuration" and double click again on "Shutdown" in the right window.
4. In the new window, click "add", "Browse", locate your "ntosboot.bat" file & click "Open".
5. Click "OK", "Apply" & "OK" once again to exit.
6. From the Start menu, select "Run..." & type "devmgmt.msc".
7. Double click on "IDE ATA/ATAPI controllers"
8. Right click on "Primary IDE Channel" and select "Properties".
9. Select the "Advanced Settings" tab then on the device or 1 that doesn't have 'device type' greyed out select 'none' instead of 'autodetect' & click "OK".
10. Right click on "Secondary IDE channel", select "Properties" and repeat step 9.
11. Reboot your computer.
Posted by windows team at 5:34 AM 0 comments
BIOS Update Procedure
All latest Motherboards today, 486/ Pentium / Pentium Pro etc.,ensure that upgrades are easily obtained by incorporating the system BIOS in a FLASH Memory component. With FLASH BIOS, there is no need to replace an EPROM component. Once downloaded, the upgrade utility fits on a floppy disc allowing the user to save, verify and update the system BIOS. A hard drive or a network drive can also be used to run the newer upgrade utilities. However, memory managers can not be installed while upgrading.
Most pre-Pentium motherboards do not have a Flash BIOS. The following instructions therefore do not apply to these boards. If your motherboard does not have a Flash BIOS (EEPROM) you will need to use an EPROM programmer to re-program the BIOS chip. See your dealer for more information about this.
Please read the following instructions in full before starting a Flash BIOS upgrade:
A. Create a Bootable Floppy (in DOS)
•With a non-formatted disk, type the following:
format a:/s
•If using a formatted disk, type:
sys a:
This procedure will ensure a clean boot when you are flashing the new BIOS.
B. Download the BIOS file
•Download the correct BIOS file by clicking on the file name of the BIOS file you wish to download.
•Save the BIOS file and the Flash Utility file in the boot disk you have created. Unzip the BIOS file and the flash utility file. If you don't have an "unzip" utility, download the WinZip for Windows 95 shareware/ evaluation copy for that one time use from _www.winzip.com or _www.pkware.com. Most CD ROMs found in computer magazines, have a shareware version of WinZip on them.
•You should have extracted two files:
Flash BIOS utility eg: flash7265.exe (for example)
BIOS eg: 6152J900.bin (example)
Use the latest flash utility available unless otherwise specified (either on the BIOS update page or in the archive file). This information is usually provided.
C. Upgrade the System BIOS
During boot up, write down the old BIOS version because you will need to use it for the BIOS backup file name.
Place the bootable floppy disk containing the BIOS file and the Flash Utility in drive a, and reboot the system in MS-DOS, preferably Version 6.22
•At the A:> prompt, type the corresponding Flash BIOS utility and the BIOS file with its extension.
For example:
flash625 615j900.bin
•From the Flash Memory Writer menu, select "Y" to "Do you want to save BIOS?" if you want to save (back up) your current BIOS (strongly recommended), then type the name of your current BIOS and its extension after FILE NAME TO SAVE: eg: a:\613J900.bin
Alternatively select "N" if you don't want to save your current BIOS. Beware, though, that you won't be able to recover from a possible failure.
•Select "Y" to "Are you sure to program?"
•Wait until it displays "Message: Power Off or Reset the system"
Once the BIOS has been successfully loaded, remove the floppy disk and reboot the system. If you write to BIOS but cannot complete the procedure, do not switch off, because the computer will not be able to boo, and you will not be given another chance to flash. In this case leave your system on until you resolve the problem (flashing BIOS with old file is a possible solution, provided you've made a backup before)
Make sure the new BIOS version has been loaded properly by taking note of the BIOS identifier as the system is rebooting.
For AMI BIOS
Once the BIOS has been successfully loaded, remove the floppy disk and reboot the system holding the "END" key prior to power on until you enter CMOS setup. If you do not do this the first time booting up after upgrading the BIOS, the system will hang.
BIOS Update Tips
note:
1.Make sure never to turn off or reset your computer during the flash process. This will corrupt the BIOS data. We also recommend that you make a copy of your current BIOS on the bootable floppy so you can reflash it if you need to. (This option is not available when flashing an AMI BIOS).
2. If you have problems installing your new BIOS please check the following:
Have you done a clean boot?
In other words, did you follow the above procedure for making a bootable floppy? This ensures that when booting from "A" there are no device drivers on the diskette. Failing to do a clean boot is the most common cause for getting a "Memory Insufficient" error message when attempting to flash a BIOS.
If you have not used a bootable floppy, insure a clean boot either by
a) pressing F5 during bootup
b) by removing all device drivers on the CONFIG.SYS including the HIMEM.SYS. Do this by using the EDIT command.
Have you booted up under DOS?
Booting in Windows is another common cause for getting a "Memory Insufficient" error message when attempting to flash a BIOS. Make sure to boot up to DOS with a minimum set of drivers. Important: Booting in DOS does not mean selecting "Restart computer in MS-DOS Mode" from Windows98/95 shutdown menu or going to Prompt mode in WindowsNT, but rather following the above procedure (format a: /s and rebooting from a:\).
Have you entered the full file name of the flash utility and the BIOS plus its extension?
Do not forget that often you will need to add a drive letter (a:\) before flashing the BIOS. Example: when asked for file name of new BIOS file which is on your floppy disk, in case you're working from c:\ your will need to type a:\615j900.bin, rather than 615j900.bin only.
Posted by windows team at 5:32 AM 0 comments
Drag Files into Notepad
Drag Files into Notepad
You can read the text from any file by dragging the file from Windows Explorer into notepad. For example, if you wanted to read a .cfg file, you can open notepad and then drag the file into notepad to read the configurations stored in the file.
Here's how to do it:
1. Open Notepad by clicking Start-->All Programs-->Accessories-->Notepad.
2. Open Windows Explorer and browse to the file from which you want to read text.
3. Drag and drop the file from Windows Explorer into Notepad. The text in the file appears in notepad.
Posted by windows team at 5:29 AM 4 comments
Bandwidth Explained
This is well written explanation about bandwidth, very useful info.
BandWidth Explained
Most hosting companies offer a variety of bandwidth options in their plans. So exactly what is bandwidth as it relates to web hosting? Put simply, bandwidth is the amount of traffic that is allowed to occur between your web site and the rest of the internet. The amount of bandwidth a hosting company can provide is determined by their network connections, both internal to their data center and external to the public internet.
Network Connectivity
The internet, in the most simplest of terms, is a group of millions of computers connected by networks. These connections within the internet can be large or small depending upon the cabling and equipment that is used at a particular internet location. It is the size of each network connection that determines how much bandwidth is available.
For example, if you use a DSL connection to connect to the internet, you have 1.54 Mega bits (Mb) of bandwidth. Bandwidth therefore is measured in bits (a single 0 or 1). Bits are grouped in bytes which form words, text, and other information that is transferred between your computer and the internet.
If you have a DSL connection to the internet, you have dedicated bandwidth between your computer and your internet provider. But your internet provider may have thousands of DSL connections to their location. All of these connection aggregate at your internet provider who then has their own dedicated connection to the internet (or multiple connections) which is much larger than your single connection.
They must have enough bandwidth to serve your computing needs as well as all of their other customers. So while you have a 1.54Mb connection to your internet provider, your internet provider may have a 255Mb connection to the internet so it can accommodate your needs and up to 166 other users (255/1.54).
Traffic
A very simple analogy to use to understand bandwidth and traffic is to think of highways and cars. Bandwidth is the number of lanes on the highway and traffic is the number of cars on the highway. If you are the only car on a highway, you can travel very quickly. If you are stuck in the middle of rush hour, you may travel very slowly since all of the lanes are being used up.
Traffic is simply the number of bits that are transferred on network connections. It is easiest to understand traffic using examples. One Gigabyte is 2 to the 30th power (1,073,741,824) bytes. One gigabyte is equal to 1,024 megabytes. To put this in perspective, it takes one byte to store one character. Imagine 100 file cabinets in a building, each of these cabinets holds 1000 folders. Each folder has 100 papers. Each paper contains 100 characters - A GB is all the characters in the building. An MP3 song is about 4MB, the same song in wav format is about 40MB, a full length movie can be 800MB to 1000MB (1000MB = 1GB).
If you were to transfer this MP3 song from a web site to your computer, you would create 4MB of traffic between the web site you are downloading from and your computer. Depending upon the network connection between the web site and the internet, the transfer may occur very quickly, or it could take time if other people are also downloading files at the same time. If, for example, the web site you download from has a 10MB connection to the internet, and you are the only person accessing that web site to download your MP3, your 4MB file will be the only traffic on that web site. However, if three people are all downloading that same MP at the same time, 12MB (3 x 4MB) of traffic has been created. Because in this example, the host only has 10MB of bandwidth, someone will have to wait. The network equipment at the hosting company will cycle through each person downloading the file and transfer a small portion at a time so each person's file transfer can take place, but the transfer for everyone downloading the file will be slower. If 100 people all came to the site and downloaded the MP3 at the same time, the transfers would be extremely slow. If the host wanted to decrease the time it took to download files simultaneously, it could increase the bandwidth of their internet connection (at a cost due to upgrading equipment).
Hosting Bandwidth
In the example above, we discussed traffic in terms of downloading an MP3 file. However, each time you visit a web site, you are creating traffic, because in order to view that web page on your computer, the web page is first downloaded to your computer (between the web site and you) which is then displayed using your browser software (Internet Explorer, Netscape, etc.) . The page itself is simply a file that creates traffic just like the MP3 file in the example above (however, a web page is usually much smaller than a music file).
A web page may be very small or large depending upon the amount of text and the number and quality of images integrated within the web page. For example, the home page for CNN.com is about 200KB (200 Kilobytes = 200,000 bytes = 1,600,000 bits). This is typically large for a web page. In comparison, Yahoo's home page is about 70KB.
How Much Bandwidth Is Enough?
It depends (don't you hate that answer).
But in truth, it does. Since bandwidth is a significant determinant of hosting plan prices, you should take time to determine just how much is right for you. Almost all hosting plans have bandwidth requirements measured in months, so you need to estimate the amount of bandwidth that will be required by your site on a monthly basis If you do not intend to provide file download capability from your site, the formula for calculating bandwidth is fairly straightforward:
Average Daily Visitors x Average Page Views x Average Page Size x 31 x Fudge Factor
If you intend to allow people to download files from your site, your bandwidth calculation should be:
[(Average Daily Visitors x Average Page Views x Average Page Size) +(Average Daily File Downloads x Average File Size)] x 31 x Fudge Factor
Let us examine each item in the formula:
Average Daily Visitors - The number of people you expect to visit your site, on average, each day. Depending upon how you market your site, this number could be from 1 to 1,000,000.
Average Page Views - On average, the number of web pages you expect a person to view. If you have 50 web pages in your web site, an average person may only view 5 of those pages each time they visit.
Average Page Size - The average size of your web pages, in Kilobytes (KB). If you have already designed your site, you can calculate this directly.
Average Daily File Downloads - The number of downloads you expect to occur on your site. This is a function of the numbers of visitors and how many times a visitor downloads a file, on average, each day.
Average File Size - Average file size of files that are downloadable from your site. Similar to your web pages, if you already know which files can be downloaded, you can calculate this directly.
Fudge Factor - A number greater than 1. Using 1.5 would be safe, which assumes that your estimate is off by 50%. However, if you were very unsure, you could use 2 or 3 to ensure that your bandwidth requirements are more than met.
Usually, hosting plans offer bandwidth in terms of Gigabytes (GB) per month. This is why our formula takes daily averages and multiplies them by 31.
Summary
Most personal or small business sites will not need more than 1GB of bandwidth per month. If you have a web site that is composed of static web pages and you expect little traffic to your site on a daily basis, go with a low bandwidth plan. If you go over the amount of bandwidth allocated in your plan, your hosting company could charge you over usage fees, so if you think the traffic to your site will be significant, you may want to go through the calculations above to estimate the amount of bandwidth required in a hosting plan.
Posted by windows team at 5:26 AM 0 comments
All About Spyware
All About Spyware
There are a lot of PC users that know little about "Spyware", "Mal-ware", "hijackers", "Dialers" & many more. This will help you avoid pop-ups, spammers and all those baddies.
What is spy-ware?
Spy-ware is Internet jargon for Advertising Supported software (Ad-ware). It is a way for shareware authors to make money from a product, other than by selling it to the users. There are several large media companies that offer them to place banner ads in their products in exchange for a portion of the revenue from banner sales. This way, you don't have to pay for the software and the developers are still getting paid. If you find the banners annoying, there is usually an option to remove them, by paying the regular licensing fee.
Known spywares
There are thousands out there, new ones are added to the list everyday. But here are a few:
Alexa, Aureate/Radiate, BargainBuddy, ClickTillUWin, Conducent Timesink, Cydoor, Comet Cursor, eZula/KaZaa Toptext, Flashpoint/Flashtrack, Flyswat, Gator, GoHip, Hotbar, ISTbar, Lions Pride Enterprises/Blazing Logic/Trek Blue, Lop (C2Media), Mattel Brodcast, Morpheus, NewDotNet, Realplayer, Songspy, Xupiter, Web3000, WebHancer, Windows Messenger Service.
How to check if a program has spyware?
The is this Little site that keeps a database of programs that are known to install spyware.
Check Here: http://www.spywareguide.com/product_search.php
If you would like to block pop-ups (IE Pop-ups).
There tons of different types out there, but these are the 2 best, i think.
Try: Google Toolbar (http://toolbar.google.com/) This program is Free
Try: AdMuncher (http://www.admuncher.com) This program is Shareware
If you want to remove the "spyware" try these.
Try: Lavasoft Ad-Aware (http://www.lavasoftusa.com/) This program is Free
Info: Ad-aware is a multi spyware removal utility, that scans your memory, registry and hard drives for known spyware components and lets you remove them. The included backup-manager lets you reinstall a backup, offers and multi language support.
Try: Spybot-S&D (http://www.safer-networking.org/)
This program is Free
Info: Detects and removes spyware of different kinds (dialers, loggers, trojans, user tracks) from your computer. Blocks ActiveX downloads, tracking cookies and other threats. Over 10,000 detection files and entries. Provides detailed information about found problems.
Try: BPS Spyware and Adware Remover (http://www.bulletproofsoft.com/spyware-remover.html) This program is Shareware
Info: Adware, spyware, trackware and big brotherware removal utility with multi-language support. It scans your memory, registry and drives for known spyware and lets you remove them. Displays a list and lets you select the items you'd like to remove.
Try: Spy Sweeper (http://www.webroot.com/wb/products/spysweeper/index.php) This program is Shareware
Info: Detects and removes spyware of different kinds (dialers, loggers, trojans, user tracks) from your computer.
The best scanner out there, and updated all the time.
Try: HijackThis (http://www.spywareinfo.com/~merijn/downloads.html) This program is Freeware
Info: HijackThis is a tool, that lists all installed browser add-on, buttons, startup items and allows you to inspect them, and optionally remove selected items.
If you would like to prevent "spyware" being install.
Try: SpywareBlaster (http://www.wilderssecurity.net/spywareblaster.html) This program is Free
Info: SpywareBlaster doesn`t scan and clean for so-called spyware, but prevents it from being installed in the first place. It achieves this by disabling the CLSIDs of popular spyware ActiveX controls, and also prevents the installation of any of them via a webpage.
Try: SpywareGuard (http://www.wilderssecurity.net/spywareguard.html) This program is Free
Info: SpywareGuard provides a real-time protection solution against so-called spyware. It works similar to an anti-virus program, by scanning EXE and CAB files on access and alerting you if known spyware is detected.
Try: XP-AntiSpy (http://www.xp-antispy.org/) This program is Free
Info: XP-AntiSpy is a small utility to quickly disable some built-in update and authentication features in WindowsXP that may rise security or privacy concerns in some people.
Try: SpySites (http://camtech2000.net/Pages/SpySites_Prog...ml#SpySitesFree) This program is Free
Info: SpySites allows you to manage the Internet Explorer Restricted Zone settings and easily add entries from a database of 1500+ sites that are known to use advertising tracking methods or attempt to install third party software.
If you would like more Information about "spyware".
Check these sites.
http://www.spychecker.com/
http://www.spywareguide.com/
http://www.cexx.org/adware.htm
http://www.theinfomaniac.net/infomaniac/co...rsSpyware.shtml
http://www.thiefware.com/links/
http://simplythebest.net/info/spyware.html
Usefull tools...
Try: Stop Windows Messenger Spam 1.10 (http://www.jester2k.pwp.blueyonder.co.uk/j...r2ksoftware.htm) This program is Free
Info: "Stop Windows Messenger Spam" stops this Service from running and halts the spammers ability to send you these messages.
----------------------------------------------------------------------------
All these softwares will help remove and prevent evil spammers and spywares attacking your PC. I myself recommend getting "spyblaster" "s&d spybot" "spy sweeper" & "admuncher" to protect your PC. A weekly scan is also recommended
Free Virus Scan
Scan for spyware, malware and keyloggers in addition to viruses, worms and trojans. New threats and annoyances are created faster than any individual can keep up with.
http://defender.veloz.com// - 15k
Finding . is a Click Away at 2020Search.com
Having trouble finding what you re looking for on: .? 2020Search will instantly provide you with the result you re looking for by drawing on some of the best search engines the Internet has to offer. Your result is a click away!
http://www.2020search.com// - 43k
Download the BrowserVillage Toolbar.
Customize your Browser! Eliminate Pop-up ads before they start, Quick and easy access to the Web, and much more. Click Here to Install Now!
http://www.browservillage.com/ - 36k
Hope this is useful
Posted by windows team at 5:22 AM 0 comments
Hidden Commands in Firefox
Have you ever tried these hidden commands in the address bar of your Firefox.If not,then try it..
about: A simple prompt without any parameter will display the Mozilla “about” information. Since it’s accessible from the top menus as well, it’s not quite a hidden feature.
about:buildconfig Obviously, it will show the build platform configuration and parameters
 about:cache Will display info and statistics regarding your disk’s cache, including the name of your cache’s directory and a list of the entries you can find there. By default, Firefox doesn’t allow you to view the cached webpages, so this can be an useful option.
about:cache Will display info and statistics regarding your disk’s cache, including the name of your cache’s directory and a list of the entries you can find there. By default, Firefox doesn’t allow you to view the cached webpages, so this can be an useful option.
about:config Oh look, many many info. Indeed, it’s the most complex and meaningful of them all. Careful on what you plan to change here, your browser won’t run properly after if you play with the wrong things.
about:plugins Of course, what is Firefox without it’s powerful extensions? This option will display detailed information about all the plugins installed for Mozilla Firefox.
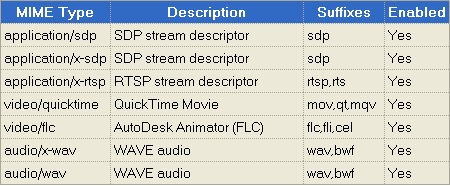
about:credits It’s time to give the credit to whoever deserves it. There’s an alphabetically sorted list of all the people that gave their contribution to the development of Firefox.
about:Mozilla This is a weird thing. It will display the so-called “Book of Mozilla”. Something similar was present in Netscape too. There’s actually no real book although the quotations might give you that impression.

If you have other similar tricks then don't hesitate to comment here.
Thanks 'our-tricks'
Posted by windows team at 5:19 AM 0 comments
The 13 Best Torrent Downloaders
 Acquisition is torrent client, which allows to share files with tens of millions of Mac and Windows users around the planet. Requirements: Mac OS X 10.4 Tiger.
Acquisition is torrent client, which allows to share files with tens of millions of Mac and Windows users around the planet. Requirements: Mac OS X 10.4 Tiger.
Opera is the fastest, and most secure free Web browser available. You don’t need a separate BitTorrent application to download large files. Simply click a torrent link and start the download.
Arctic Torrent is an Open Source minimal BitTorrent client. It won’t have all the pretty features that other Torrent apps have, but focuses on low memory and cpu usage. Because it was written in C++, you dont get the high memory requirements of Java or high CPU usage of Python. Arctic is tested on Windows XP and should work on 2000, XP, and 2003 in 32-bit and 64-bit. It uses Unicode and thus will not run on Windows 9x.
Azureus implements the BitTorrent protocol using java language and comes bundled with many invaluable features for both beginners and advanced users. Runs on all operating systems.
BitComet is a BitTorrent/HTTP/FTP download management software, which is powerful, fast, very easy-to-use, and completely free. It contains many advanced features for BitTorrent download and extends its leading BitTorrent technology to HTTP/FTP to accelerate downloading up to 5 - 10 times faster, or more. Runs on Windows 2000/XP/2003/Vista. Windows 98/Me can use the ZIP version.
Torrent Swapper is an open source sociable peer to peer file-sharing client based on the Bittorrent protocol that is ideal for high-speed distribution of large files that has a basic understanding of human friendships, of user tastes in content, and of Internet connectivity between users. Torrent Swapper supports simultaneous downloads, download queue, selected downloads in torrent package, fast-resume, disk cache, speed limits, port mapping, proxy, ip-filter, etc. Works with Linux, OS X and Windows.
BitLord is a powerful C++ BitTorrent Client. BitLord is a p2p file-sharing freeware program fully compatible with Bittorrent, which is the most popular p2p protocol designed for high-speed distribution of 100MB or GB sized files. It supports simultaneous downloads, download queue, selected downloads in torrent package, fast-resume, chatting, disk cache, speed limits, port mapping, proxy, ip-filter, etc.Works with Windows 98/ME/2000/XP/2003.
μTorrent is a BitTorrent client that includes bandwidth prioritization, scheduling, RSS auto-downloading and Mainline DHT (compatible with BitComet). Additionally, µTorrent supports the Protocol Encryption joint specification and peer exchange. Windows only.
BitSpirit is a powerful and easy-to-use BitTorrent client. It supports simultaneous downloads, download queue, UPNP port-maping, NAT traversal(UDP transport), select downloads from multiple files torrent package, disk cache, chatting with other peers, torrent market,ip-filter, etc. Runs on Windows 98/Me/2000/XP/2003.
BitTornado is a BitTorrent client. Works on Windows, Linux, OS X, BSD.
BitTorrent for Windows brings together BitTorrent’s proven expertise in networking protocols with µTorrent’s efficient implementation and compelling UI to create a better BitTorrent client.
BitTyrant is a new, protocol compatible BitTorrent client that is optimized for fast download performance. Works with Linux, OS X, and Windows.
FlashGet is a leading download manager and has the highest amount of users on the Internet. It uses MHT(Multi-server Hyper-threading Transportation) technique, supports various protocols and has excellent document management features. FlashGet is a freeware without any adware or spyware.
Labels: http://www.blogger.com/img/gl.italic.gif
Posted by windows team at 5:14 AM 22 comments
Bulk Editing of .rar,.zip.mp3 etc
lets us say you have just download a new album or gamebut all the files are .xxx and you need them to bezip's, rar's, mp3's etc.....then do the following
-create a new folder-put all the files needing editing in the new folder-then goto "run" in the start menu-type in CMD and click ok
-the next thing needsa few bits of old dos commands-you need to navagate CMD to the folder whree the files are-you can do this by 1st getting the total adress of the folder-and then typing it in cmd with a "cd" in frount
cd c:\xxx\yyy\ccc\
once you in the folder where the files are you can move on
note: u can check in the right folder by typing dir to get a list of files
-now type in....QUOTE
rename *.* *.zip
Note: change the zip to what ever the extention needs to be (.rar, .mp3 etc)
all done
you should hv now changed the .* to what ever you needed
note: to exit CMD type in "exit"
Posted by windows team at 5:13 AM 0 comments
Convert .pptx to .ppt and .docx to .doc without Office 2007
Convert your .pptx to .ppt and .docx to .doc without installing Microsoft Office 2007.This is an online service provided by Zamzar.They now support latest microsoft documents.
The full list of supported formats is below:
- html - Hypertext Markup Language
- odp - OpenDocument presentation
- pdf - Portable Document Format
- png - Portable Network Graphic
- ppt - Microsoft Powerpoint Presentation
- ps - Postscript document
- swf - Macromedia Flash Format File
Simply drag the button below onto your "Bookmarks Toolbar"
This button provided in their website could be used to convert files from all your favourite websites at the click of a button.
Posted by windows team at 5:11 AM 15 comments
Update to solve Windows Vista USB errors
Microsoft finally releases updates to solve Windows Vista USB related errors.
Issues that are fixed includes:
- Stop errors occur on a Windows-based computer that has 2GB or more of RAM and is using an NVIDIA nForce USB controller
- Problems after you resuming a Windows Vista-based computer from sleep or from hibernation
- Error message when you try to put a Windows Vista-based computer to sleep or into hibernation
- After you use the Safely Remove Hardware option to remove a built-in optical drive from a portable Windows Vista-based computer, you may be unable to reconnect the drive
- Error message in the Usbhub.sys process when you wake a Windows Vista-based computer from sleep or from hibernation
- A USB device may no longer work correctly after Windows Vista resumes from sleep or from hibernation
- Recording quality is poor when you use a USB microphone on a Windows Vista-based computer that has 4 GB of RAM or more
- A USB composite device does not work after you disable and then enable the device in Device Manager on a computer that is running Windows Vista
- When you connect a USB multifunction printer device to a Windows Vista-based computer, a second instance of the printer object is created, and the first instance no longer works
- Error message on a Windows Vista-based computer that is running a USB composite device
- The Safely Remove Hardware feature and the Windows Explorer "Eject" command do not work correctly with an Apple iPod that is connected to a Windows Vista-based computer
- A USB device takes a long time to resume from "selective suspend" mode on a Windows Vista-based computer that uses UHCI USB controllers
- When you resume a Windows Vista-based computer from sleep, you may experience unexpected behavior from a USB device.
Download it here
Windows Vista, 32-bit versions  Download the 941600 package now.
Download the 941600 package now.
Windows Vista, 64-bit versions  Download the 941600 package now.
Download the 941600 package now.
Posted by windows team at 5:08 AM 3 comments